Cybersecurity threats are evolving faster than ever, and staying informed is no longer optional; it’s essential. As businesses, governments, and individuals rely more heavily on digital systems, cybercriminals continue to find new ways to exploit vulnerabilities. From sophisticated phishing attacks to AI-powered malware, understanding today’s most dangerous cybersecurity threats can help you stay one step […]
In the current digital age, our mobile devices are forever vibrating with notifications from friends and family, companies, and strangers calling. More than one dozen calls are important; for instance, calls about medical appointments or delivery notifications; however, the majority of them could be just spam, telemarketing, or outright scams. For this reason, phone number […]
A Gentle and Clear Explanation of Spotube’s Safety As soon as individuals find out about Spotube, an open-source music streaming client that’s lightweight and easy to use, the very first question that pops up in their minds is: “Is Spotube safe?” It is a reasonable inquiry, in particular, because there are a great number of […]
In the world of peer-to-peer file sharing, torrenting remains one of the most popular methods for distributing digital content. Among the myriad of trackers available, IPTorrents stands out as a private BitTorrent tracker that has both a dedicated following and a controversial reputation. In this article, we’ll explore IPTorrents, its working model, community aspects, legal […]
Introduction In the world of online gaming, privacy and security are becoming increasingly critical. One controversial service that has sparked both concern and debate is xResolver. This website allows users to look up IP addresses tied to usernames on gaming platforms like Xbox and PlayStation. While some see it as a tool for accountability, others […]
Identity theft is growing faster than ever. Every 14 seconds, someone in the U.S. falls victim to digital theft. Thieves don’t even need to touch your wallet anymore—they can steal card information wirelessly. This is where Wallet Defender comes in. What Is Wallet Defender? Wallet Defender is a credit card-sized RFID and NFC blocking device […]
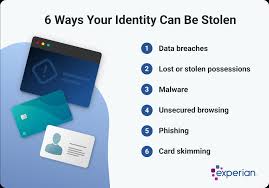
Identity theft online is becoming increasingly common. But what does it really mean when your identity is stolen online, and how should you respond? What Is Identity Theft Online? When someone impersonates another person on the internet, it is called identity theft online. The motives can vary widely, from committing financial fraud to carrying out […]